The killall Command in Linux
In this tutorial, we’ll cover the killall command in Linux. We recently posted a tutorial on the kill command in Linux where we covered the usage and the functionality of the command. Today, we’ll go over how to use the…
In this tutorial, we’ll cover the killall command in Linux. We recently posted a tutorial on the kill command in Linux where we covered the usage and the functionality of the command. Today, we’ll go over how to use the…
Docker is an application that simplifies the process of managing application processes in containers. Containers let you run your applications in resource-isolated processes. Containers are similar to Virtual Machines, but are much less resource-intensive, as they only need the absolute…
Let’s have a look at a really simple to use firewall, the UFW firewall. As a system administrator, it is our duty to make sure that the systems we work on are secured from attackers. There are multiple methods to…
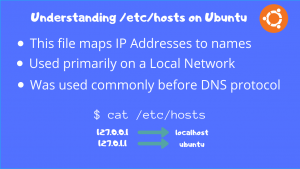
The hosts’ file is an extremely useful albeit small text file that stores host names with associated IP addresses. It is basically a mapping from hostnames to IP addresses. Any network protocol uses this mapping to convert hostnames to numeric…
CouchDB is a free and open-source fault-tolerant database made and maintained by the Apache Software Foundation. It is a very good choice for a NoSQL type database, where you do not want a relational database. In this tutorial, we shall…
A DNS cache (sometimes called a DNS resolver cache) is a temporary database, maintained by a computer’s operating system, that contains records of all the recent visits and attempted visits to websites and other internet domains. You may want to…