Hello folks, In this article, We will see how to scan vulnerabilities using Nikto.
Nikto is an open-source command-line vulnerability scanner that scans web servers for potentially dangerous files, outdated versions, server configuration files, and other problems. It is a popular, easy-to-use, and very powerful pen-testing tool.
It is not a stealthy tool, which means it will look in the fastest way possible, and it will get detected by an IDS or Intrusion Detection System (if you need a stealthy tool, try nmap on Kali instead). Nikto comes with SSL support, Full HTTP Proxy support, and saves reports in plain text, HTML, XML, etc. Let’s discuss in detail how to install Nikto in Kali Linux and use it to scan web servers for vulnerabilities.
Features:
- SSL, HTTP, and Proxy support
- Cookies support
- Outputs in plain text, HTML or CSV
- specific server software checks
Also read: How to install and use anonsurf on Kali Linux?
Installing Nikto
Nikto comes pre-installed with Kali Linux installation. To run Nikto, Go to Drawer > Vulnerability scanner > Nikto or type Nikto in a terminal window. If it is not installed on your system, you can install it by executing the following command:
sudo apt update
sudo apt install nikto
Basic Scanning
nikto -h <ip_address or host_name>
To scan an SSL-enabled website, Execute the following command:
nikto -h <host_name> -ssl
nikto -h <ip_address or host_name> -port <port_number>
nikto -h example.com -output /path/to/file.name
Scanning IP Addresses
sudo ifconfig
To get the network range, Run ipcalc. if you don’t have ipcalc, Install it by running the following command:
sudo apt install ipcalc
ipcalc 192.168.0.48
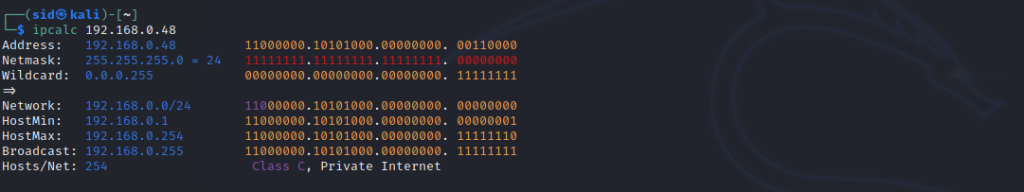
Now, Use Nmap to Scan for running services in the network range. We will scan port 80 with the range above. Port 80 is the default port. -oG is used to extract hosts that are up and running. The output will be saved to a file named output.txt.
nmap -p 80 192.168.0.0/24 -oG output.txt
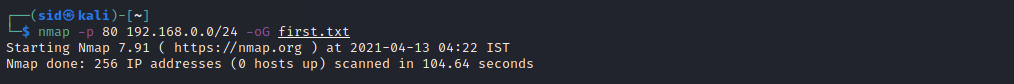
Now, Execute the following command to see the output stored in the output.txt file:
cat nullbyte.txt | awk '/Up$/{print $2}' | cat >> targetIP.txt

Here, awk is used to filter the IP addresses that are up. In the end, the cat command is used to save the filtered output to a new file named targets.txt.
To send the output to nikto, Execute the following command:
nikto -h targetIP.txt
Summary
So, We discussed how to scan vulnerabilities using nikto in Kali Linux. There are many other options and detailed scanning can be done using many other options. You can refer to the manpage to know more about nikto by clicking here.





