The root user enjoys the privilege of being able to access just about anything in the Linux system. While disabling root login is an authentication strategy that might boost security, people still debate whether it’s truly effective or not. Don’t worry, in this tutorial we’re going to walk you through different ways to prevent root access, making sure we keep authentication in mind.
How to Enable Root Login in Linux
By default, Ubuntu disallows logging into root via the GUI login. Though not recommended, you can enable it in Ubuntu by using the following command to set a new password for the account. The same command is applicable to almost any Linux distribution.
sudo passwd root
Now you can enter a new password and then proceed to use the -u command option with the command to unlock the root user.
sudo passwd -u root
Now you can log in as a root account via the su command below and use the whoami command to verify the user.
su root
whoami
Disable Root Login in Linux
Most of the methods that we’re listing here are pretty much accessible for every Linux distribution.
Note: Before disabling the login for the root in any Linux server or distribution, it is crucial to establish an alternative admin account with the ability to execute ‘su’ or ‘sudo’ commands. This precautionary measure prevents root access from being compromised and safeguards you from inadvertently locking yourself out of your system or losing control over crucial management functions. Possessing an admin account with ‘su’ or ‘sudo’ privileges enables you to efficiently manage system resources, adjust settings, and perform vital tasks. Without this access, an attacker could exploit your inability to execute essential operations, thereby jeopardizing the stability and security of your Linux system.
Let’s go over all the available methods one by one.
1. Disable Root Login in Linux with passwd Command
To disable the root login, you can use the passwd command below:
sudo passwd -l root
This will lock the password for the root user and you won’t be able to access the root account with its password until a new one is set.
2. Disable Root Login Using the usermod Command
Similar to the command above, we can use the usermod command to lock the account using the -L command option.
sudo usermod -L root
3. Changing the Login Shell to /usr/sbin/nologin
In this case, what we’re going to do is to change the default root shell to nologin instead of bash. So whenever someone logs in to the root account even with the correct password, the account will automatically exit the shell.
Two ways to set nologin shell:
- Edit the /etc/passwd file manually
- Use the usermod command to set the default shell
We recommend using the usermod command as it is cleaner than manually editing the file, but we’ll still demonstrate both methods here.
Editing the /etc/passwd file manually:
sudo nano /etc/passwd
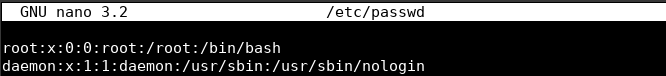
Now you can change the part which says “/bin/bash” adjacent to the root user, to “/usr/sbin/nologin”.
Use the usermod command to set the default shell:
Now let’s come to a cleaner way to disable root login. This will be done by using the usermod command along with the -s option to set the default shell.
sudo usermod -s /usr/sbin/nologin root
Once you do this, the default shell will be set and you can verify the same by doing a cat /etc/passwd.
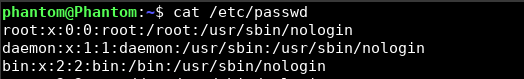
Great! Now you know that the root user cannot log in to any terminal. If you do try to login after this, you’ll get the below message.
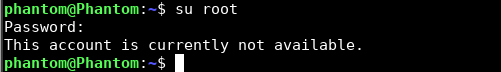
4. Disable Root SSH Login
What if you do not want to disable the root login for the entire operating system but only want to disable access via SSH servers? Well, you can do that by simply editing the /etc/ssh/sshd_config file and disable root login from there.
By default, it’s set to prohibit-password which means you cannot log in to the account with a password and can only make use of the Keys. We can edit this to say no to completely disallow root access for SSH users.
Edit the SSH config file by using the command below:
sudo nano /etc/ssh/sshd_config
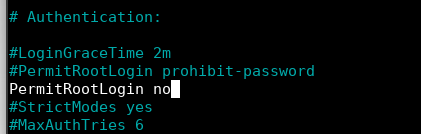
And find the line that says PermitRootLogin. Now you can uncomment the same line and edit it, or add another line with your desired option. In my case, I’ve simply written the same thing on a new line.
5. Restricting access to the root account services via PAM
In Linux, restricting root user privileges to services via PAM (Pluggable Authentication Modules) is an effective way to enhance system security and limit the attack surface. To achieve this, you can modify the PAM configuration files for specific services, typically located in the /etc/pam.d/ directory. For instance, you can use the ‘pam_listfile’ module to create an access control list of allowed or denied users, ensuring only authorized personnel can access critical services.
To demonstrate how to restrict root access to a specific service using the pam_listfile module, let’s assume we want to limit root access to the “sshd” service. First, you need to create an access control list, which is simply a list of allowed or denied users. Here’s a sample terminal command to create a file with a list of allowed users:
echo -e "user1\nuser2\nuser3" | sudo tee /etc/allowed_users
Now, open the PAM configuration file for the “sshd” service:
sudo nano /etc/pam.d/sshd
Add the following line at the beginning of the file to configure the pam_listfile module:
auth required pam_listfile.so item=user sense=allow file=/etc/allowed_users onerr=fail
Save and close the file. This configuration ensures that only the users listed in /etc/allowed_users can access the “sshd” service. Root access will be denied unless you explicitly add “root” to the list of allowed users.
Conclusion
Well, that’s about it. These are just some of the quick and easy methods to disable root login in Linux that you can work with. For the most part, the first two methods will serve all your purposes. But if you need help with a specific situation, comment below and we can help you out with it better.
