In this article, we’ll discuss how to install a certificate in a Linux system, its importance, and its use cases. Nowadays, in a world where cyberattacks are becoming more common, it is crucial to take safeguards to protect your online activity. One approach to do this on a Linux system is to install certificates.
You can skip directly to the installation guide by clicking here.
What are Certificates?
Digital certificates serve as identity proof for entities like websites, servers, and organizations. They are utilized to create an encrypted, secure connection between two parties online. The name of the entity, the public key that is used for encryption, the certificate’s expiration date, and the name of the certificate authority (CA) that issued it are all included in the certificates.
Why is there a need to install certificates?
The communication between devices and servers is secured in large part by certificates. Your device and the server exchange digital certificates to create a secure connection when you connect to a website or server. These certificates confirm the server’s identity and guarantee that the data being delivered is encrypted and secure from third-party interception.
In server environments, where security is of the utmost concern, Linux systems are frequently used. Hence, to ensure that your online activities are secure, you must install certificates on your Linux machine.
When and Why You Need to Install Certificates Explicitly in Linux?
Generally, certificates are already installed in the system & browser. But, in some cases we need to explicitly install a certificate in Linux, here are some of the general cases:
- The certificate is for a private network: If the certificate is issued for a private network or an internal server, it may not be recognized by your browser’s default list of trusted root certificates. In this case, you may need to install the certificate explicitly to establish a secure connection.
- The certificate is issued by a non-trusted CA: If the certificate is issued by a CA that is not included in your browser’s list of trusted root certificates, you may need to install the certificate explicitly to establish a secure connection.
- The certificate has been revoked: If a certificate has been revoked by the issuing CA, your browser may not recognize the revocation and may still trust the certificate. In this case, you may need to install a new certificate explicitly to establish a secure connection.
Ways for Obtaining Linux Certificates
To obtain certificates for Linux, you can use a certificate authority such as Let’s Encrypt or a commercial provider, or generate self-signed certificates for testing purposes. It’s crucial to choose the appropriate certificate type and ensure that your certificates remain up-to-date and secure. Some of the ways are:
- Let’s Encrypt: Free and automated certificate authority that provides domain-validated certificates. The Certbot tool automates the process.
- Commercial Certificate Authorities: Provide SSL/TLS certificates with different levels of validation at a cost. Examples include DigiCert, GlobalSign, and Comodo.
- Self-signed Certificates: Generated for testing or internal use. Not recommended for public-facing websites. Can be useful for internal testing and development purposes. Can be generated using OpenSSL.
Steps to Install Certificates in Linux
Let’s now look at the methods for installing a certificate in Linux
Method 1: Using Linux Command Line
This method involves using the command line in Linux to install a certificate. It’s a powerful method that allows for precise control over the installation process.
Step 1: Open the terminal window (Ctrl + Shift + T)
Open the terminal application on your Linux system.
Step 2: Copy the certificate to the system
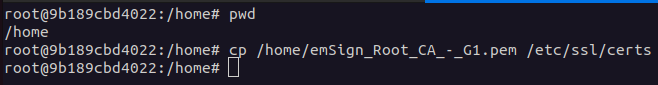
The certificate should be copied to the system using this command:
sudo cp /path-to-certificate.crt /etc/ssl/certs/
Use the path of your certificate file in place of /path-to-certificate.crt.
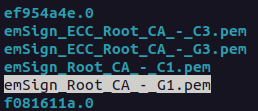
Step 3: Update the certificate authority list
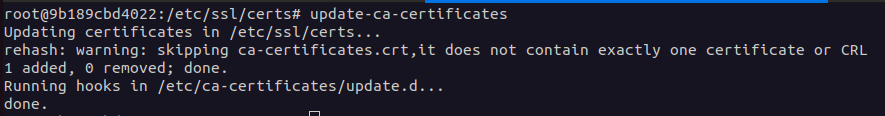
Use the command sudo update-ca-certificates to update the certificate authority list on your system.
update-ca-certificates
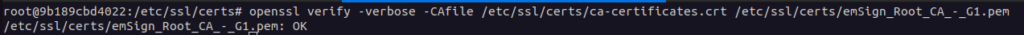
Step 4: Verify the certificate installation
OpenSSL is used to verify the authenticity of a CA certificate in Linux by checking its signature against the public key of the issuing CA, ensuring that it has not been tampered with and is still valid.
openssl verify -verbose -CAfile /etc/ssl/certs/ca-certificates.crt /etc/ssl/certs/certificate.crt
Replace /etc/ssl/certs/certificate.crt with the path to your certificate file.
Method 2: Using Linux System GUI
If you do not prefer the command-line method, you can also use the GUI to install certificates on Linux.
Step 1: Locate the Certificate File in Directory
Open your file manager and go to the directory where your certificate is located.
Step 2: Install the Certificate
Open the certificate file by double-clicking on it, then click “Install Certificate” and follow the on-screen directions to finish the installation.
Method 3: Using a Web Browser
In this method, you need to access the certificate through the web browser, and you can export it as a file, which can be installed using Method 1 or 2.
Step 1: Accessing the Certificate
Open the web browser and navigate to the website where the certificate is located. And, on the address bar, click the lock symbol.
Step 2: Exporting the Certificate
Depending on the certificate’s validity, click “Certificate (Valid)” or “Certificate (Invalid)” & Choose “Details” from the menu. To save the certificate file, select the “Export” button.
Step 3: Installing the Certificate
To install the certificate, follow the instructions for method 1 or method 2.
Conclusion
Installing certificates in Linux is essential for ensuring the security of your online activities. You can easily install certificates using the GUI, command line, or web browser by following the instructions provided in this article. To ensure the highest level of security, never use certificates that you don’t trust from reputable Certificate Authorities.
How do I generate a CSR (Certificate Signing Request) for an SSL certificate on a Linux server?
To generate a CSR for an SSL certificate on a Linux server, you can use the following command: openssl req -new -newkey rsa:2048 -nodes -keyout yourdomain.key -out yourdomain.csr. Make sure to replace “yourdomain” with your actual domain name.
How can I install an SSL certificate on my Apache server running on Linux?
To install an SSL certificate on an Apache server in Linux, you need to update your Apache configuration file to include the paths to your certificate and key files. You can then configure your virtual host to use the SSL certificate for secure connections.
What is the best practice for securing my Linux system with an SSL certificate?
To secure your Linux system with an SSL certificate, ensure that the certificate chain is correctly configured, the private key file is kept secure, and the SSL configuration on your Apache server is set up properly. Regularly check your logs for any SSL-related errors and keep your certificate files in a safe location.
Where can I find the configuration file for Apache server on Ubuntu to install an SSL certificate?
On Ubuntu, the Apache server configuration file for SSL certificates is usually located at /etc/apache2/sites-available/default-ssl.conf. You can edit this file to include the paths to your SSL certificate and key files.
What steps should I follow to configure SSL on my Apache server on RHEL (Red Hat Enterprise Linux)?
To configure SSL on an Apache server in RHEL, you will need to edit the httpd.conf file and add the necessary directives for SSL configuration. Ensure that you correctly specify the paths to your SSL certificate, key file, and any intermediate certificates that may be required.
