The purpose of API security is to ensure that API requests are authenticated, authorized, validated, and cleansed while the service is under load. API security differs from ordinary web servers in that a modern application or service has various API endpoints that use multiple protocols and request formats. Still, typical web servers only need to protect a few basic ports and requests.
API security is provided not only by network security rules but also by well-coded APIs. Security also plays an important role in application security testing as it processes and rejects incorrect and malicious inbound requests to ensure the confidentiality, availability, and integrity of the data and resources exposed.
Most Common API Security Risks
When designing and implementing a complete API security testing plan or updating an API, the following API security risks should be addressed:
Broken Object-Level Authorization
Broken object-level authorization occurs when a request has the ability to access or modify data that the requestor should not have access to, such as via tampering with a request identifier.
Excessive Data Exposure
API answers to requests frequently return more information than is relevant or necessary. Even if the data is not exposed to the user, it can be easily inspected, potentially exposing critical information.
Improper Asset Management
API development and deployment are typically quick, and proper documentation is frequently overlooked in the scramble to offer new or updated APIs. This results in overlooked vulnerabilities like exposed and ghost endpoints and an incomplete understanding of how the older APIs work.
Lack of Resources and Rate Limiting
Due to a lack of resources and rate limitations, API endpoints are frequently exposed to the internet, rendering them vulnerable to DoS and brute-force attacks if no restrictions on the number or amount of requests exist.
Injection flaws
If request data is not properly parsed and validated, an attacker may use a command or SQL injection attack to obtain access to it or execute malicious instructions without authorization.
Mass Assignment
The mass assignment issue happens in APIs that automatically channel user input to objects or program variables. While this functionality makes code development easier, some users may initialize and overwrite server-side variables, putting the application at risk. Attackers take advantage of this primarily by guessing and providing additional object characteristics when creating requests.
Securing APIs with Best Practices for API Security
The following best practices may help in the development and maintenance of an organization’s API security:
Using an API Gateway
An API gateway separates the client interface from a collection of backend APIs, providing a centralized resource for API service availability and scalability. In addition to managing numerous API services, the API management platform covers common functions such as telemetry, rate restriction, and user authentication to ensure internal service security.
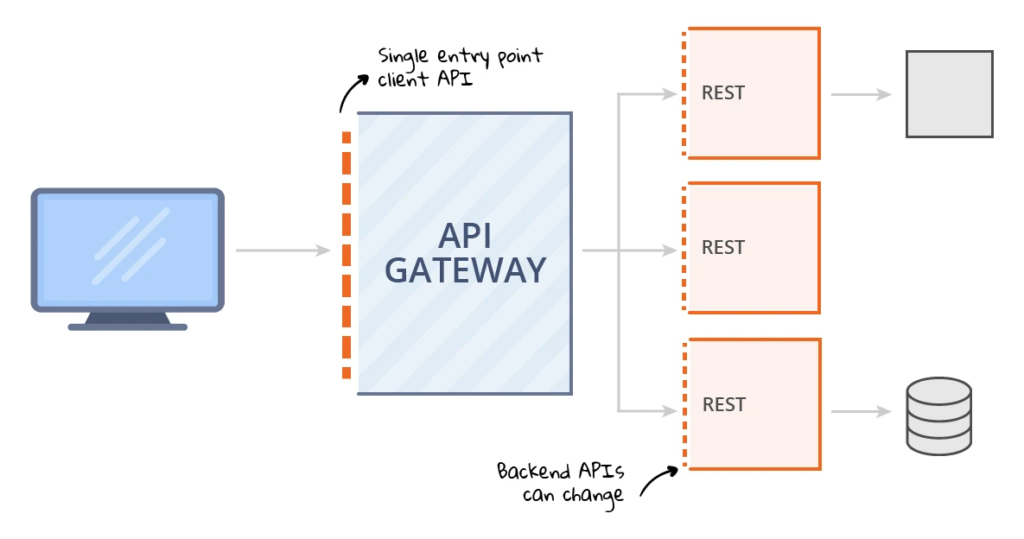
The gateway serves as a reverse proxy gatekeeper, accepting all API calls, coordinating the resources needed to support them, and returning the necessary results after authentication.
Authenticate and Authorize
To limit access to API resources, you must thoroughly identify all linked users and devices. Client-side apps are frequently used to validate clients using tokens in the API call. To authenticate API traffic and set access control rules or grant types that dictate which users, groups, and roles can access specific API services, use protocols such as OAuth 2.0, OpenID Connect, and JSON web tokens.
Implement Sufficient Input Validation
API client data should not be trusted in general because the authentication server may execute a malicious script from unauthenticated users or application services. Security teams should implement input validation protocols on the client and server sides to avoid this issue from cropping up.
Use Rate-limiting
Rate-limiting helps administer REST API security by preventing DoS and brute force attacks. Soft limitations are set by developers in some APIs, allowing clients to exceed request restrictions for a short period. Setting timeouts is a simple API security recommended practice that can handle both synchronous and asynchronous queries.
Use Throttling
Throttling is the process of putting an API into a temporary state that allows it to assess each request. It is widely used to combat spam or to prevent misuse or denial-of-service attacks. Therefore, two major considerations must be taken when developing the throttle function: how much data should be allowed per user and when the restriction should be enforced.
Validate the Data
Never assume that API data has been properly cleansed or checked. Instead, implement your own server-side data cleaning and validation methods to avoid common injection issues and cross-site request forgery attacks. Debugging tools such as Postman and Chrome DevTools can assist in examining the data flow of the API and tracking problems and abnormalities.
Scan for API Vulnerabilities
To ensure the long-term security of API services, it is necessary to enable API automatic scanning, discover vulnerabilities, and patch them at all phases of the program lifecycle.
Use HTTPS or TLS for REST APIs
HTTPS and Transport Layer Security (TLS) are secure methods of sending encrypted data between web browsers and servers. HTTPS protects authentication credentials in transit, in addition to other types of information. Every API should use HTTPS for integrity, secrecy, and authenticity as one of the most important practices. Furthermore, security teams should consider adopting mutually authenticated client-side certificates, which provide additional protection for critical data and services.
Conclusion
APIs are vulnerable to attacks in various ways, and the potential for weaknesses in the API design is enormous. As a result, securing API security is critical. The security of APIs can be ensured by a number of procedures, several of which are listed above. So, to protect the security of your APIs from outside threats and exploitations, you need to be aware of the reliable resources, expertise, and practices that may be used. In this post, we covered the most common API security threats and how to tackle them with security best practices.





