Kubernetes is undoubtedly the most preferred orchestration platform with more than 70-80% of organizations using it in one way or the other. With the increase in its popularity, protecting the clusters has also become crucial in recent times.
Kubernetes for most of the configurations provides basic security by default, for instance, IP-based security for clusters. However, when it comes to advanced security measures, you need to integrate them yourself. Kubernetes doesn’t provide them. Thus, it is essential to mitigate security risks using third-party tools.
Disclosing known vulnerabilities can help minimize risk across the IT industry. Hence open-source could be a great option. Compared to managed security tools, open-source scanning tools provide a low-cost option to swiftly implement security testing while avoiding vendor lock-in.
Let us explore some tools that can help you find vulnerabilities and misconfigurations in your Kubernetes cluster.
Kubescape Panel
Kubescape is an open-source tool that helps you assess the security, vulnerabilities, and configuration of your cluster. It supports YAML files and can detect misconfigurations according to multiple frameworks.
After scanning and analyzing your cluster, it will generate a PDF or JSON report with the risk analysis. Regularly scanning your clusters and YAML files is ideal since it identifies all the vulnerabilities that must be addressed right away.
You can start scanning by running the command:
kubescape scan –submit –enable-host-scan –verbose
Thereafter, you can submit the scan results to the Kubescape portal. You can head to Kubescape and create an account. Then select “configuration scanning” on the side pane. On scrolling down, you can find your account number. To push your results to the portal, run:
kubescape scan –submit –account=YOUR_ACCOUNT_NUMBER
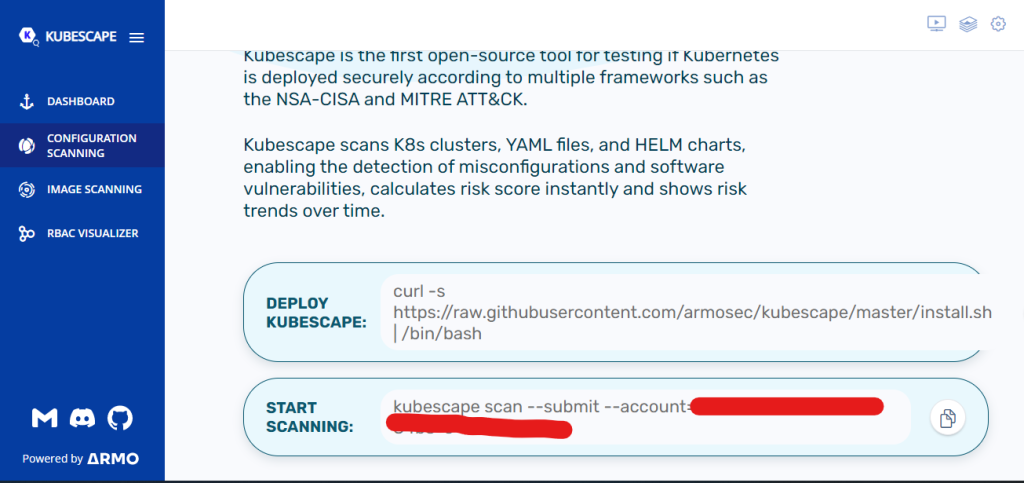
The ability to store and access scan results will help you track security improvements and patches.
Kube Bench
Kube Bench is an open-source tool by Aqua Security that allows you to perform tests in Kubernetes to confirm that you’re following the Center for Internet Security (CIS) best practices. Kube Bench is a Go application that can be deployed as a container.
These tests work with many Kubernetes versions and are defined in YAML job files that can be easily modified and extended to output test results in JSON format.
Kube Bench points out errors in test results and makes recommendations on how to fix them. It also works well with automated tools to guarantee that data is appropriately encrypted both in transit and at rest and that deployment follows least privilege principles.
Kube Bench is an excellent tool for discovering Kubernetes non-compliance issues. Kube Bench 0.50 added support for changing kubeconfig locations for kube-controller and scheduler. To run Kube Bench in AKS, execute:
docker run –rm -v `pwd`:/host aquasec/kube-bench:latest install ./kube-bench
Kubeaudit
Developed by Shopify, Kubeaudit is a command-line tool that assesses Kubernetes clusters for standard security policies. It is written in Go and can be installed on local machines with a single command. It has multiple auditing modes, including manifest, local, and cluster.
The “auditors” in Kubeaudit are tests that can be executed simultaneously or individually. It examines the Kubernetes cluster against a set of audits, including whether there are any gaps that allow privilege escalation, whether any cluster image is misconfigured, or if the root account is disabled for the system or not.
It not only checks for vulnerabilities in the cluster but also gives advice on how to fix them. Each “auditor” provides in-depth information as well as suggested practices to implement in your system.
You can execute Kubeaudit by running the following command:
kubeaudit all -f “/path/to/config_or_manifest”
Kube Scan
Octarine’s Kube Scan is a risk management tool for Kubernetes. It searches Kubernetes clusters and assigns a risk score to each workload, with 0 representing low risk and 10 representing high danger. The Kubernetes Common Configuration Scoring System (KSCCSS) framework is used to generate the risk score.
It is comparable to the CVSS. It calculates a risk score based on more than 30 security parameters such as Kubernetes policies, capabilities, and privilege levels, as well as a risk baseline. The ease of exploitation or the high impact and breadth of exploitation are also factors in the risk score.
Kube Scan can be run from the command line and has a user-friendly online interface for identifying and displaying risk information. You can also add unique rules to the KCCSS framework design.
Once you install it, it scans the workloads currently running in the cluster and then generates a detailed risk management report.
Kube-hunter
Kube-hunter is another open-source Kubernetes vulnerability scanner developed by Aqua Security and written in Python. This tool goes further than Kube Bench, analyzing Kubernetes pods and clusters outside of the CIS procedures to find potentially dangerous flaws before they are exploited by attackers by enabling the user to write custom module that can be executed from local machines, remotely or even from within the cluster in both active and passive modes.
It adds identification and penetration testing tools to Kube Bench’s CIS rules to help find potential security issues in the Kubernetes cluster. Kube-hunter scans vulnerabilities in a variety of ways, including remote, interlace, and network, executed locally or in a cluster.
It must be downloaded as a binary zip format and run using pip directly on a local PC with network access to the cluster. Alternatively, Kube-hunter can be easily installed in a Kubernetes environment by executing it as a pod within the cluster.
Conclusion
For successful monitoring and robust systems, selecting the correct tool is critical. Some of the tools mentioned above allow you to do more than just monitor; they also allow you to manage, troubleshoot, and trace. Much like the metrics you use, tools should be carefully selected and used based on your and your company’s needs.